Security Architecture Review for Enterprise Cyber Resilience
- Identify design gaps
- reduce cyber risk
- Align with global frameworks and regional regulations

How Our Security Architecture Review Strengthens Your Security
Our Security Architecture Review identifies structural weaknesses, eliminates visibility gaps, and aligns your security design with business objectives, risk appetite, and regulatory expectations across UAE and African markets.
Unified & Resilient Architecture
Fragmented security controls across cloud, on-prem, and hybrid environments are consolidated into a cohesive, defense-in-depth architecture designed to withstand modern attack scenarios.
Risk-Aligned Control Design
Security controls are evaluated and realigned based on business impact, threat exposure, and risk priority ensuring protection efforts focus on what matters most to leadership
Board-Ready Visibility & Roadmap
Leadership receives clear, executive-level insights into architectural risks, control gaps, and remediation priorities, supported by a practical, phased roadmap for measurable risk reduction.
Secure the Architecture That Protects Your Business
Discuss your environment, compliance needs, and risk concerns with an experienced security architect.
Why Security Architecture Matters for Business Leadership
Expanding attack surface increases enterprise risk
Cloud adoption, SaaS platforms, APIs, and remote work environments have dramatically expanded the digital attack surface. Without a well-designed security architecture, security controls become fragmented, leaving gaps that attackers can exploit across networks, identities, and data flows.
Complex environments demand architectural oversight, not tools alone
Modern enterprises operate across hybrid and multi-cloud environments. Security tools deployed without architectural alignment fail to provide consistent protection, increasing exposure to ransomware, credential abuse, and lateral movement attacks.
Regulatory pressure is rising across UAE and Africa
Regulations such as NESA, DESC, ADGM, POPIA, NDPR, and Kenya’s Data Protection Act require demonstrable security governance. A strong security architecture ensures compliance is built into systems rather than addressed reactively during audits.
Hidden design weaknesses create silent business risk
Many breaches occur not due to missing tools, but because of poor system design, excessive trust relationships, and misconfigured access controls. These architectural flaws remain invisible without structured review and threat modeling.
Leadership accountability continues to increase
Boards and senior leadership are now expected to understand cyber risk at a strategic level. Security architecture reviews provide the clarity needed to meet governance, oversight, and fiduciary responsibilities.
Security architecture enables confident business growth
A resilient, scalable architecture allows organizations to expand into new markets, adopt new technologies, and support digital transformation while maintaining control, resilience, and regulatory readiness.
Clear architecture supports better investment decisions
Leadership gains visibility into where security investments reduce real risk, ensuring budgets are spent strategically rather than reactively.

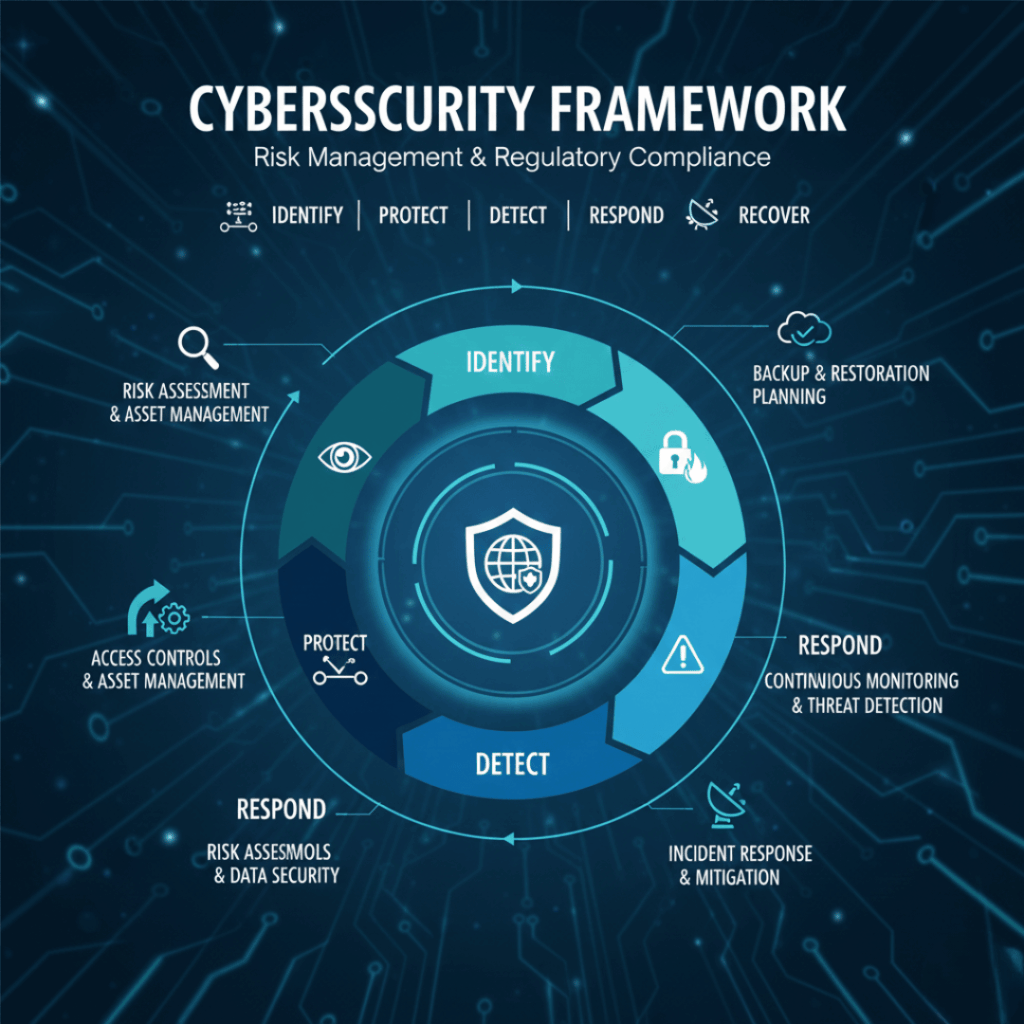
Our Security Architecture Review Approach
Current-State Architecture Assessment
We begin by assessing the existing security architecture across network, cloud, endpoint, identity, and data layers. This includes mapping data flows, trust boundaries, and system dependencies to understand how information moves across the organization.
Threat Modeling & Risk Analysis
We conduct threat modeling based on real-world attack scenarios relevant to the business and industry. We analyze how attackers could exploit architectural weaknesses, focusing on attack surface exposure, privilege escalation, and lateral movement risks.
Control Gap & Design Weakness Identification
We identify gaps between current controls and security best practices. This includes assessing defense-in-depth failures, excessive trust relationships, and misalignment with Zero Trust principles.
Future-State Secure Architecture Design
We design a future-state security architecture that is practical, scalable, and cost-aware. The recommended architecture supports secure cloud and hybrid environments, aligns with business growth plans, and provides a clear roadmap for phased implementation and measurable risk reduction.
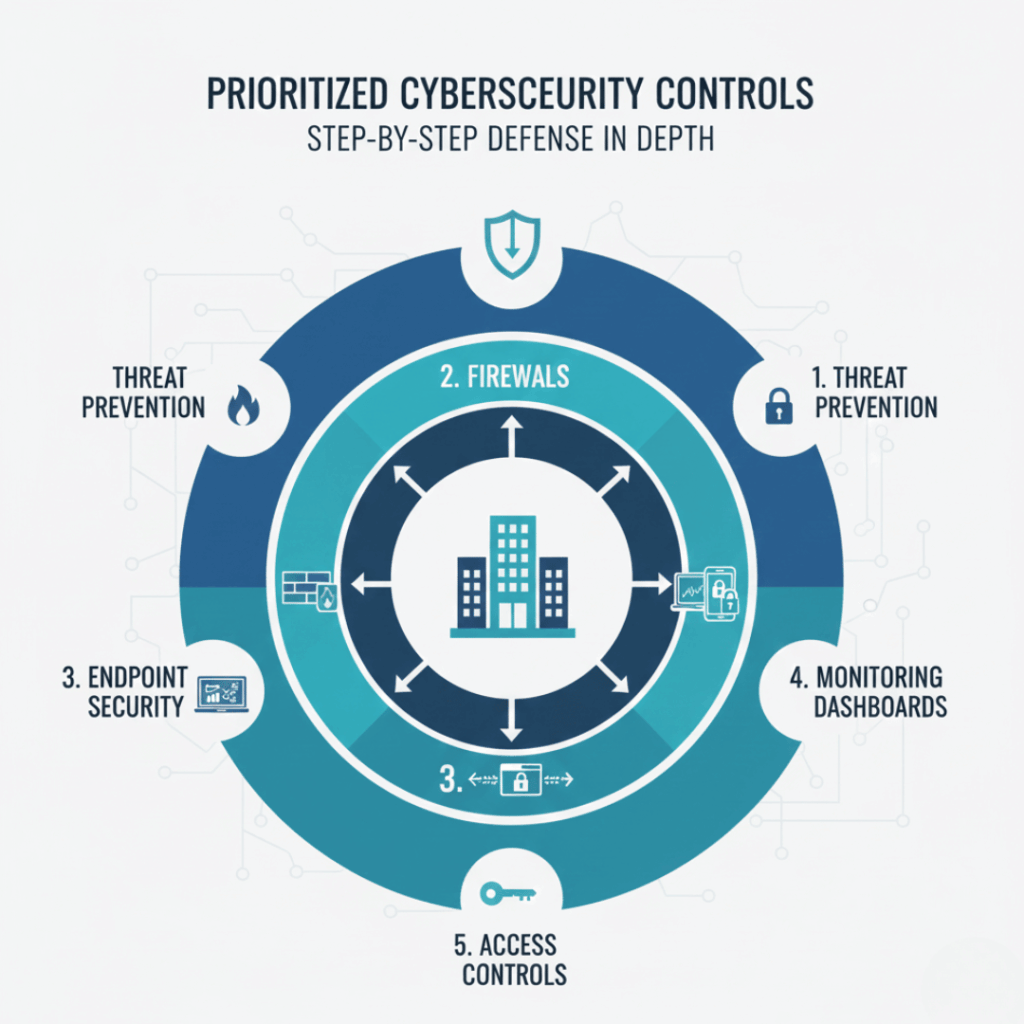
Our Core Service Matrix
High-Level
Architecture Review
Evaluate the overall security architecture to identify major design risks, trust boundaries, and control alignment gaps.
Cloud and Network
Architecture Deep Dive
Perform an in-depth assessment of cloud, network, and identity architectures to uncover hidden weaknesses and misconfigurations.
Continuous Architecture Validation Zero Trust Roadmap
Provide ongoing architecture validation with a structured Zero Trust roadmap to support long-term security maturity and resilience.
Frameworks and Standards We Align With
NIST Cybersecurity Framework
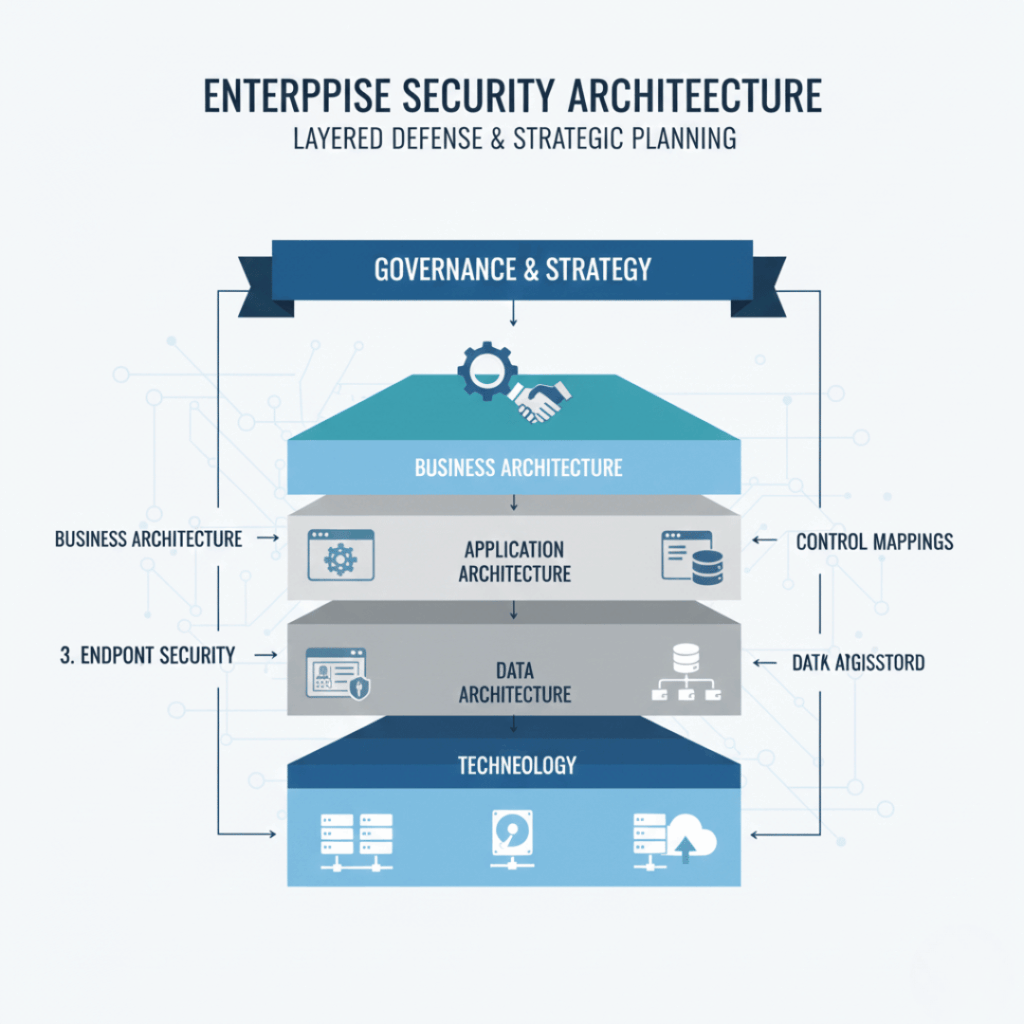
SABSA & TOGAF architecture
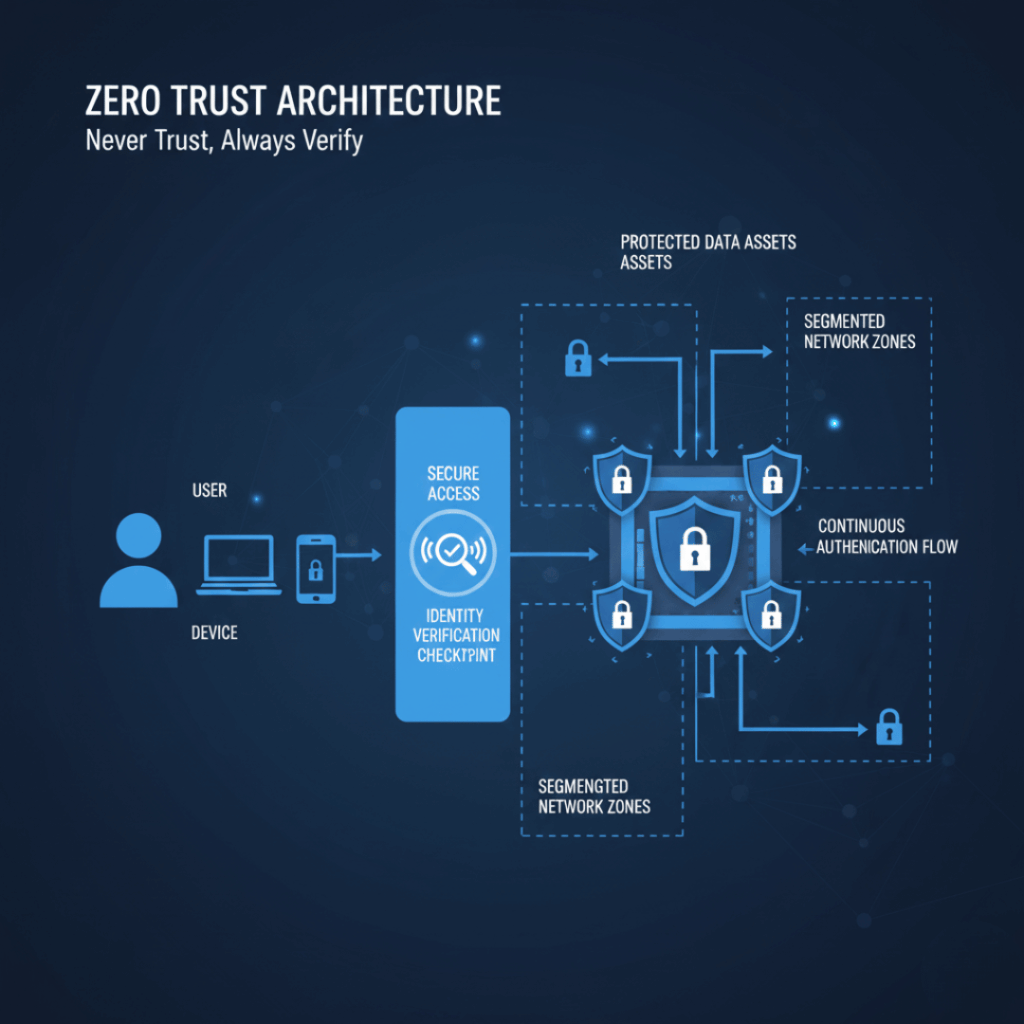
Zero Trust Architecture principles
Designed for Organizations That Demand Strong Cyber Governance
Mid-to-large enterprises
Organizations operating multiple systems, applications, and infrastructure layers benefit from a structured security architecture that ensures controls are integrated, scalable, and resilient as the business grows.
Cross-border and multinational organizations
Enterprises expanding across regions often face fragmented security controls and inconsistent risk management. A unified security architecture review helps standardize protection across geographies and operational units.
Regulated industries with strict compliance
Companies in sectors such as finance, fintech, healthcare, and technology face heightened regulatory scrutiny and data protection requirements. A security architecture review ensures that security controls are designed to meet ISO 27001, NIST, and regional regulatory standards proactively.
UAE and Africa-based organizations
Businesses operating within the UAE or across African markets must navigate diverse cybersecurity and data protection regulations. This service supports alignment with local and cross-border regulatory frameworks while maintaining consistent security governance.
Leadership teams seeking governance-level clarity
Boards, founders, and senior leadership teams gain clear visibility into architectural risks, security priorities, and remediation roadmaps, enabling informed decision-making and stronger oversight.
Organizations planning growth
Businesses preparing for cloud adoption, system modernization, or market expansion can ensure security is built into the architecture rather than added reactively.
Why Choose Us for Security Architecture Review
Certified cybersecurity leadership you can trust
Our Security Architecture Reviews are led by certified cybersecurity professionals with real-world experience designing and governing enterprise security programs.
Deep expertise in UAE and African regulatory environments
We bring strong regional knowledge across UAE and African cybersecurity and data protection regulations.
Vendor-neutral, business-first recommendations
Our approach is independent of security product vendors. We focus on architecture design, control effectiveness, and risk reduction not on selling tools.
Executive-friendly and board-ready reporting
We translate complex technical findings into clear, decision-ready insights. Leadership receives concise reports that highlight architectural risks, priorities, and remediation paths, supporting governance, oversight, and informed investment decisions.
Practical and implementable architecture designs
We balance security requirements with operational constraints, ensuring recommendations can be implemented without disrupting business operations.
Enterprise-grade security architecture consulting
We provide end-to-end cybersecurity architecture consulting, covering cloud, hybrid, network, identity, and data protection layers to deliver a unified enterprise security review.
Focus on measurable risk reduction and ROI
Every recommendation is prioritized based on risk impact and business value, helping organizations achieve tangible improvements in security posture and resilience.

Build a Stronger Security Architecture Before Risks Become Breaches
Identify hidden design weaknesses, reduce enterprise cyber risk, and align your security architecture with global standards and regional regulations before attackers exploit the gaps.
FAQs
How is a Security Architecture Review different from a security audit or penetration test?
A Security Architecture Review focuses on the design and structure of your security controls across systems, networks, cloud, and identities. Unlike audits, which check compliance, or penetration tests, which simulate attacks, this review identifies architectural weaknesses that enable breaches and provides long-term, strategic remediation guidance.
How long does a Security Architecture Review take?
The duration typically ranges from two to six weeks, depending on the size and complexity of the environment. This includes architecture mapping, control assessment, threat modeling, and delivery of an executive-level report with prioritized recommendations.
Will this review support ISO 27001 certification or audits?
Yes. The review maps your security architecture against ISO 27001 and related frameworks, helping identify gaps before audits. This reduces compliance risks and strengthens evidence for certification and regulatory assessments.
Do you cover cloud, on-prem, and hybrid environments?
Absolutely. The review includes cloud platforms, on-prem infrastructure, hybrid environments, SaaS applications, and identity systems to ensure consistent security across all operating models.
Is this service suitable for growing or scaling companies?
Yes. It is ideal for organizations experiencing growth, expansion, or digital transformation. The review ensures security scales alongside business operations without creating bottlenecks or excessive risk.
Do you provide ongoing vCISO governance support?
Yes. In addition to the review, ongoing vCISO services are available to oversee implementation, monitor architectural risks, support compliance, and provide continuous executive-level security governance.