Third-Party & Supply-Chain Risk
Management Services
Protect your organization from vendor-driven cyber, compliance, and operational risks

How Our Company Helps Manage Third-Party and Supply-Chain Risk
We help organizations understand, control, and reduce risks introduced by external partners without slowing business growth.
Vendor Risk Identification & Prioritization
We identify which suppliers, vendors, and partners pose the highest risk based on data access, system dependency, and business impact.
Security & Compliance Due Diligence
We assess vendor security practices against recognized standards and regional regulations, helping leadership ensure suppliers meet expected security and compliance levels.
Ongoing Risk Monitoring & Governance
We establish governance processes to continuously monitor third-party risk, track changes, and report risk exposure in clear, executive-friendly language.
Protect Your Business From Supplier-Driven Risk
Gain visibility into third-party exposure, meet regulatory expectations, and build a resilient, secure supply chain.
Why Third-Party & Supply-Chain Risk Matters
Third-party and supply-chain risks are no longer limited to operational or IT functions. They have become strategic business risks that directly affect governance, organizational resilience, and regulatory compliance. As organizations across the UAE and Africa increasingly rely on external vendors, cloud providers, and outsourced services, the security posture of these third parties becomes inseparable from the organization’s own risk profile.
Cyberattacks increasingly originate through vendors, suppliers, and service providers.
Threat actors often target third parties because they typically have weaker security controls and trusted access to core systems or sensitive data. A single compromised vendor can provide attackers with a pathway into critical environments, bypassing otherwise strong internal defenses.
Regulators hold organizations accountable for third-party failures.
Regulatory authorities expect organizations to exercise due diligence and ongoing oversight of their vendors. Data breaches, service outages, or compliance failures caused by third parties can result in penalties, audit findings, and enforcement actions against the organization itself, not the supplier.
Single-vendor dependency increases operational and financial exposure.
Heavy reliance on one critical supplier creates concentration risk. Vendor outages, cyber incidents, or financial instability can disrupt operations, delay services, and directly impact revenue and contractual obligations.
Supply-chain disruptions impact service availability and customer trust.
Interruptions caused by third-party failures can affect service continuity, delivery timelines, and customer experience. Repeated disruptions damage confidence among customers, partners, and regulators.
Poor vendor controls weaken the overall cybersecurity posture.
Inadequate third-party security governance undermines enterprise-wide risk management. Without consistent controls, monitoring, and accountability, supply-chain vulnerabilities can erode resilience and expose the organization to cascading cyber and operational risks.
Our Core Service Matrix
Vendor Checklist and Evaluation
We provide structured checklists and evaluation templates to assess vendors during onboarding.
Vendor Risk Register & Assessment
All identified vendor risks are documented in a centralized risk register.
Continuous Third-Party Risk Monitoring
Vendor risk is monitored on an ongoing basis through periodic reviews, risk scoring, and incident tracking.
Our Third-Party & Supply-Chain Risk Management Approach
Vendor Risk Identification & Classification
We begin by identifying all third parties and suppliers that interact with your organization’s systems, data, or operations. Vendors are segmented based on risk, considering factors such as data sensitivity, system access, and business criticality.
Vendor Due Diligence & Security Assessment
Each vendor undergoes structured cybersecurity and compliance assessments before onboarding and during engagement. These assessments evaluate security controls, data protection practices,
and regulatory readiness.
Contractual, Governance & Oversight Controls
Strong governance is embedded through security clauses and regulatory SLAs within vendor contracts. These define accountability, security expectations, and compliance obligations.
Continuous Vendor Risk Monitoring
Third-party risk does not end at onboarding. We implement ongoing vendor risk scoring, incident tracking, and periodic reassessments. Lifecycle-based vendor governance ensures risks are continuously managed as vendors, technologies, and regulations evolve.
Supply-Chain Cybersecurity & Operational Resilience
Cyber risk in logistics, IT, cloud, and outsourcing ecosystems
Digital integration has become a foundational element of how supply chains operate and exchange information. Logistics providers may integrate directly with enterprise platforms, IT and cloud vendors often have privileged system access, and outsourcing partners handle sensitive data and processes.
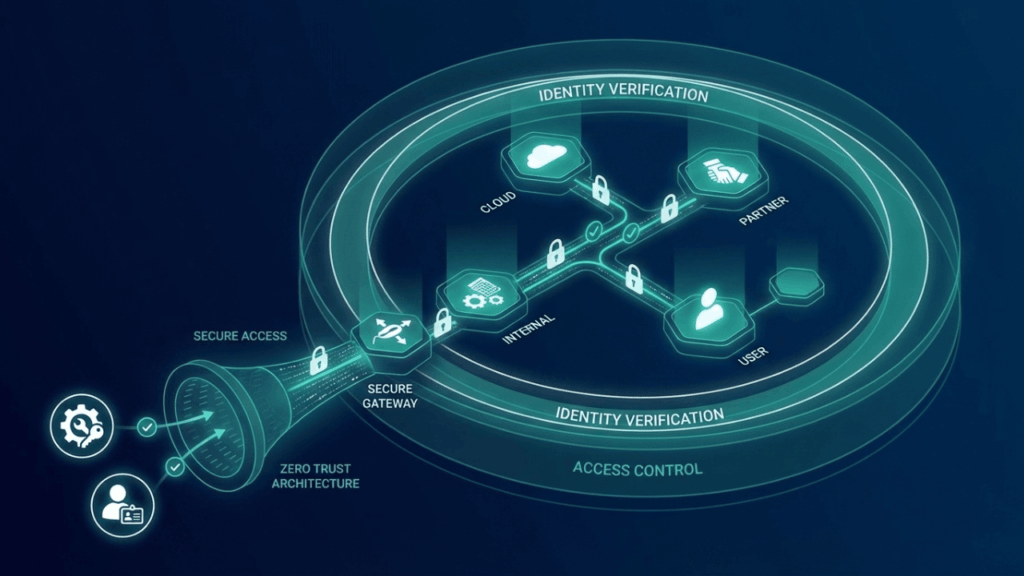
Zero Trust principles for third-party and supplier access
Traditional perimeter-based security models are no longer sufficient for supply-chain environments. Applying Zero Trust principles ensures that no third party is automatically trusted, regardless of their role or relationship.
Business continuity and supplier failure preparedness
Operational resilience requires preparing for supplier disruptions caused by cyber incidents, outages, or financial instability. This includes contingency planning, alternate supplier strategies, and clearly defined response procedures.
Business Protection That Supports Long-Term Growth
Reduced exposure to cyber incidents
By identifying high-risk vendors, enforcing security controls, and continuously monitoring supplier risk, organizations significantly reduce the likelihood and impact of cyber incidents originating from third parties.
Audit-ready vendor risk documentation
Comprehensive documentation of vendor assessments, risk classifications, and governance controls ensures organizations are always prepared for regulatory audits and internal reviews.
Stronger supply-chain resilience
Effective risk management reduces dependency on single vendors and strengthens preparedness for disruptions. Organizations can respond more quickly to supplier incidents, maintain service continuity, and protect revenue streams.
Improved executive board-level visibility
Executive dashboards and structured reporting provide leadership with clear insights into third-party and supply-chain risk exposure. This visibility enables informed decision-making, prioritization of critical risks.

Why Choose Us for Third-Party & Supply-Chain Risk
Deep expertise in UAE & African regulatory landscapes
Managing third-party and supply-chain risk requires more than technical assessments it demands regional regulatory insight, strong governance, and executive-level oversight.
Framework-driven, risk-based methodologies
Our methodologies are aligned with globally recognized frameworks such as ISO 27001, NIST, and leading third-party risk standards.
Executive-level reporting and dashboards
We translate complex third-party risk data into clear, decision-ready insights for senior leadership
Practical, implementation-focused approach
We focus on real-world implementation, not theoretical models. Our recommendations are actionable, scalable, and tailored to your operating environment.
Ongoing vCISO-led governance support
Our vCISO-led oversight ensures continuous governance, risk monitoring, and alignment with evolving regulatory and business requirements.
Secure Your Supply Chain Before It Becomes a Business Risk
Identify hidden third-party risks, strengthen governance, and protect business continuity before a supplier incidentturns into a regulatory or operational crisis.
FAQs
What is third-party and supply-chain risk?
Third-party and supply-chain risk refers to the cybersecurity, operational, and compliance risks introduced by vendors, suppliers, service providers, and outsourced partners that access your systems, data, or critical business processes. These risks extend beyond your direct control and require structured governance and oversight.
Why is third-party risk management important for regulatory compliance?
Regulators increasingly hold organizations accountable for the actions and failures of their third parties. Effective third-party risk management demonstrates due diligence, supports audit readiness, and helps meet regulatory requirements across UAE and African jurisdictions.
How do cyberattacks occur through suppliers and vendors?
Attackers often target vendors with weaker security controls and trusted system access. Once compromised, these third parties can be used as entry points to access sensitive data, disrupt operations, or bypass internal security defenses.
Which vendors should be included in third-party risk assessments?
All vendors that access sensitive data, systems, or critical operations should be assessed. Priority is given to high-risk and critical suppliers based on factors such as data sensitivity, business impact, and dependency level.
How often should third-party risk be reviewed?
Third-party risk should be assessed at onboarding and reviewed continuously. Regular reassessments, ongoing monitoring, and periodic audits ensure risks remain controlled as vendor relationships and threat landscapes evolve.
Does this service support ISO 27001, NIST, and regulatory audits?
Yes. Our approach is aligned with ISO 27001, NIST, and regional regulatory expectations, providing audit-ready documentation, executive reporting, and structured governance to support internal and external audits.
